4 Key Steps to Stopping Ransomware Attacks
How Significant is the Ransomware Problem?
In writing this blog post we reviewed data from a variety of surveys including the Verizon Data Breach Report, the Cybersecurity Insiders Survey, the Ponemon Survey Data, a survey conducted by HelpSystems in conjunction with Cybersecurity Insiders.
Key findings in the various benchmark cybersecurity surveys include:
- Only 5% of survey respondents DID NOT experience a ransomware attack.
- Malware, particularly ransomware has become one of the most destructive security threats affecting all types of organizations – the Verizon Data Breach Report supports this research and suggested 43% of all breaches affected small businesses.
- 70% of organizations believe malware and ransomware will become a larger threat to their organizations in the next year.
- 76% consider a malware attack in the next 12 months moderately to extremely likely.
- 86% percent of the survey respondents view malware and ransomware either as an extreme threat (49%) or moderate threat (37%).
- 54% consider phishing emails the most dangerous attack vector, followed by trojans with 13%.
- 75% of companies infected with ransomware were running up-to-date endpoint protection
- The World Economic Forum Report listed cyber threats as the 4th greatest risk to world economies – The Cybersecurity Insider survey confirms the perceived threat among the heads of security that they surveyed.
Exploring the Ransomware Problem
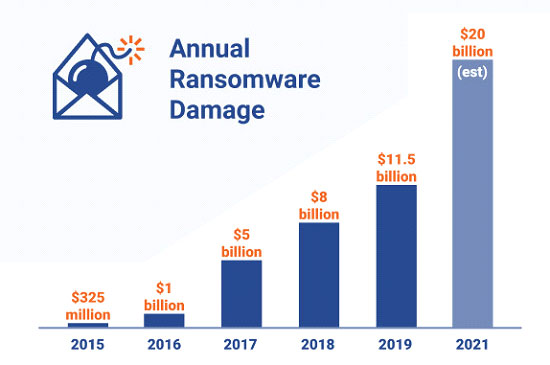
According to Dark Reading which cites a report by Cybersecurity Ventures, the Ransomware problem has now increased to over $11.5 billion in payments and damages with the number of attacks up between 200%- 300% over last year. In addition, the report suggests that the average cost of a ransomware attack last year was estimated at $141,000, up from $46,800 last year. Much of the rise in damage, increase in the number of attacks and transition in targets from corporations and individuals to easier targets like municipalities were the result of the emergence of the non-state, financially targeted attacker.
Along with the common non-tech criminal getting involved in the ransomware attack game, the rise in attacks can also be attributed to the dramatic increase in rentable malware droppers like Emotet. These droppers can be essentially hired to deliver malware of virtually any kind to targeted systems. Moreover, there has been a significant rise in black-market Software-as-a-Service networks with actual helplines for the non-technical attacker or “script kiddies” to get guidance from seasoned cyber-criminal organizations launch attacks.
In 2017, Ransomware terrorized the globe with the widespread impact of global campaigns WannaCry and NotPetya. However, after that scare, ransomware appeared to take a step back to campaigns based around cryptojacking attacks, trojan malware or credential theft. The brief pause in ransomware attacks prior to last year was clearly the calm before the storm.
How Does Ransomware Infiltrate and Lock My System and Data
Last year during a 12-month period starting in Q2 ransomware attacks increased over 365% against businesses, however, only 12% against consumers. Clearly, the transition for larger paydays for cyber-criminals had started. Interestingly, the method of attack has stayed fairly consistent throughout this new reign of terror on small businesses and municipalities.
The malware is most often delivered through phishing e-mails and now more commonly spear-phishing emails; the ransomware locks hard drives or other parts of the system that makes data assets virtually impossible to access.
While there are countless types of ransomware 3 families of the malware have done most of the damage: Dharma, Ryuk, and GandCrab.
The Dharma Ransomware
Dharma ransomware first emerged in 2016 as a variant of the Crysis ransomware and is now one of the most potent forms of ransomware in its own right. The authors of Dharma have been releasing new updates for the malware which prevent standard decryption products from being created. What makes Dharma so successful is that it spreads by targeting internet-facing ports and remote desktops.
As opposed to most ransomware attacks that leverage phishing attacks, Dharma can gain access to networks without even having to get a victim to click a link or download a malicious file from a phishing email. The malware is manually delivered by attackers who exploit Remote Desktop Protocol (RDP) services via TCP port 3389 and brute force the password to gain access to a computer.
Phobos, another devastating piece of ransomware is similar to Dharma in that it can arrive on systems in a variety of ways. It can infiltrate systems via open or insecure remote desktop protocol (RDP) connections on port 3389, brute-forced RDP credentials. Phobos operators can also leverage malicious attachments, downloads, patch exploits, and software vulnerabilities to gain access to an organization’s endpoints and network.
The Ryuk Ransomware
Ryuk ransomware is more lucrative than its predecessor Hermes. It targets large organizations and government agencies that end up paying up in large amounts. In fact, without the big payoffs, executing Ryuk attacks is not sustainable. Attacks using Ryuk involve a high degree of manual processes including direct exploitation and payment requests handled via email. Attackers won’t want to waste their time if they don’t believe they are targeting a lucrative target.
The ransomware was initially attributed to North Korea, but now researchers believe that it’s more likely to be the Russian-based organized crime group called Grim Spider which created the most devastating strain of the malware a year ago. It is estimated that Ryuk earned it’s the Russians more than $3.7 million in its first four months.
There have been a variety of high-profile attacks in just the last few months; Lake City, Florida paid $530,000 in bitcoin to cybercriminals to unlock its data in June and fired its IT manager for not protecting the organizations from the attacks. It followed an attack on another Florida city, Riviera Beach, which paid $600,000 to unlock encrypted files.
The GandCrab Ransomware
GandCrab ransomware first emerged two years ago and wreaked havoc for the next 12 months. Described by Europol as “one of the most aggressive forms of ransomware”, GandCrab was on an affiliate model, its authors leased out the ransomware in exchange for a portion of the profits.
GandCrab is distributed via multiple spreading vectors, which include spam emails, exploit kits and other affiliated malware campaigns.
GrandSoft and RIG are the two most commonly used exploit kits for distributing GandCrab along with the high number of malicious spam emails that the ransomware leverages. These spam emails trick users into opening the file contained inside the attached ZIP archive, which is generally a script that downloads the GandCrab ransomware and executes it.
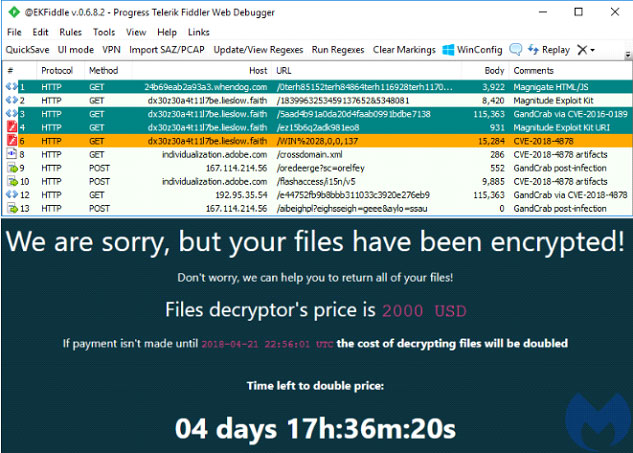
Like Dharma, when free decryption tools were released to combat GandCrab its developers released new versions. The group behind GandCrab suggested that they earned over $2 billion but have now ceased operations suggesting their first of its kind ransomware-as-a-service model has made them comfortable.
A decryption tool for the most recent version of GandCrab is available from the awesome group No More Ransom.
The 4 Step Solution to Protecting Against Ransomware Attacks
Because IT security, incident response, and cybersecurity organizations, in general, have investigated so many ransomware attacks over the past several years, we are all getting a sense of how to defend more effectively. That said, the team at SecureOps has taken cyber-defense a step further than simply having a “sense” of how to defend. They have leveraged their deep understanding of how ransomware infiltrates a system, spreads throughout a network and uses locks data and system functions to attack.
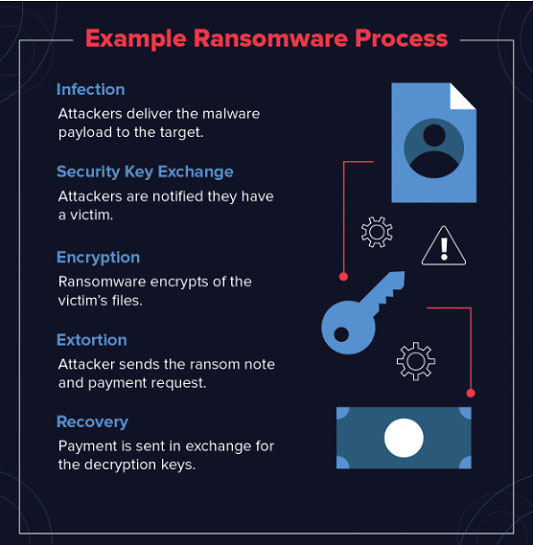
Detailing the 4 Steps Organizations Should Take to Defend Against Ransomware Attacks
In IT security we often refer to an attack as having a “Land and Expand” strategy. Meaning the cyber-criminal must figure out how to get the malware onto the system. After they “Land” the attacker must move the malware to other systems by escalating credentials or some other means to “Expand” their attack and find the most lucrative victims.
Let’s walk through how to execute the 4 steps and how they can help close the gaps that cyber-criminals use to steal billions from their victims.
Key 1 – Prevention
The prevention strategy is aimed at hardening systems or targets against attacks. Systems are reinforced against phishing attacks, RDP/Remote Access attacks, and other attacks a best practice approach to eliminating vulnerabilities. Prevention is about implementing:
- Social Engineering Training – Do not think of formal mandatory training with dozens of employees on a web conferencing call or in a meeting room weekly to understand phishing tactics. This about sending periodic e-mails making certain employees DON’T CLICK ON LINKS AND ATTACHMENTS without verifying them to some degree.
- Scan E-mails – Content scanning and filtering technology are fairly effective at identifying “known” malware from getting through an e-mail gateway.
- Install the Latest Software Patches – Yes, we understand that this isn’t breakthrough advice, however, as we all know, attackers leverage software vulnerabilities more effectively than any other attack vector to infiltrate a system.
Key 2 – Escalation
Attackers use lateral movement to pivot from the initially compromised system to other systems that hold the data that they are targeting. This privilege escalation is executed by the attacker using errors and flaws in systems to methodically obtain additional privileges as they move through the organization’s environment to ultimately compromise higher-value targets.
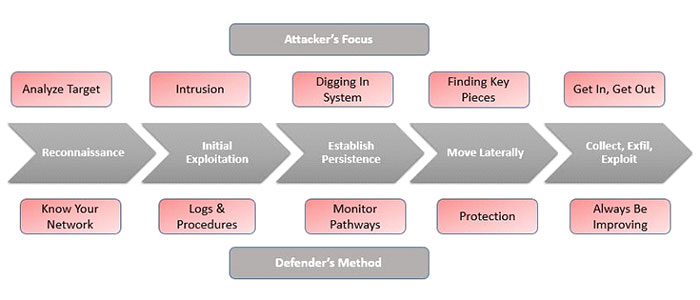
To prevent an escalation of the attack or lateral movement of the malware from one system to another you must first take your system off the network. You don’t necessarily need to shut down the system, however, it should be isolated.
A common type of attack involves stealing a security token to gain access to another device or server. ‘Pass the hash’ is an example of this, where a stolen hash is used to authenticate the attacker. Passwords should not be stored in plain text by users or systems, and password hashes should be protected to prevent attackers from easily accessing them. Also, ensure that a single account cannot grant access to all devices and components across an enterprise, particularly if those accounts are privileged.
Finally, Local and domain administrative accounts – with access to the organization’s systems and data – are powerful tools in a network. Their use should be tightly controlled and locked down as should any systems that contain PII or the personal information of employees, customers, and partners.
Also, administrators should use separate accounts; one for day-to-day business use including web browsing and emails and a privileged administrator account that should only be used on separate administration devices. This reduces the risk of an infected device being used for admin purposes.
Ultimately, administrator accounts should be prevented from browsing the web and accessing emails, and only be used when a task requires elevated permissions. The principle of ‘least privilege’ (where accounts and users have the minimum amount of access needed to perform their role) should be implemented wherever possible.
Key 3 – Recovery
The reality is that despite the advice we provided in steps 1 & 2 and we could have thrown in lots more advice discussing firewalls, SIEM’s, Log monitoring and so much more, however, cyber-attackers are still finding their way into organizations. Further, they are literally blackmailing companies for millions and in many cases destroying systems and IT environments with the malicious code.
In a Vanson Bourne survey of 500 cybersecurity decision-makers sponsored by SentinelOne last year, 48 percent said their organizations had been hit by at least one ransomware attack in the last 12 months, with the average victim hit six times and the recovery time over 33 hours on average.
Thus, how do you recover quickly from a ransomware attack? Let’ discuss two critical ways:
- Back-up Solutions – Successful backups with an effective retention policy enables organizations to recover from ransomware attacks without having to pay the ransom. Regularly performing and testing backups will help limit the impact of data or system loss and expedite the recovery process. There are offsite replication technologies that allow organizations to replace the locked data with “mirrored” or the same data which is stored offsite.
- Enhance Protection – We should say this again, “the average victim was hit 6 times” by an attack. Thus, as you replace the data on the systems that you must wipe and repair, you should re-scan the systems to make sure the malware isn’t lurking in the back-up data. Also, run a digital forensic post-mortem to understand the attack in detail to make sure you have 100% protection against the same attack. Finally, weaknesses in Microsoft’s Server Message Block (SMB) and Remote Desktop Protocol (RDP) have allowed cryptoworms to spread. Desktop applications and even Microsoft Office (Microsoft’s Dynamic Data Exchange — DDE) have been the agents of infection.
Key 4 – Improve Security Controls
Organizations are doing a far better job of implementing a security control framework such as CIS 20, NIST, and ISO. You can read more about those here – on our Security Posture Service Page – https://secureops.com/services-portfolio/security-posture-assessments/
According to Wikipedia security controls are “Security controls are safeguards or countermeasures to avoid, detect, counteract, or minimize security risks to physical property, information, computer systems, or other assets.” Good definition. Let’s look at one example:
- NIST suggests that to implement a quality vulnerability management program and patch management program that the following should be a part of any organization’s “prevention” program against malware attacks:
- Create a system inventory – identify which systems are high value
- Scan for vulnerabilities – identify which vulnerabilities on which systems need to be fixed quickly
- Automate deployment of patches – as organizations mature they can manage the vulnerability management process through automation
Conclusion
This was quite a bit of information and we didn’t want to go too deep into the recommendations. Frankly, because we understand how ransomware infiltrates systems and locks data we wanted to provide you a good 80/20 list of steps to take to prevent and mitigate a ransomware attack. That is, provide take the 20% of the most impactful steps you can take to prevent 80% of the attacks and damage from the attacks.
As we’ve said in the past, a good risk management program is based on the fact that you cannot prevent all attacks. To do so, the cost would bankrupt most companies. Implement cost-effective preventative measures and resiliency procedures, however, be vigilant about automating and executing the controls and process that you do invest in.
We hope you enjoy the post and please reach out to us if we can help you and your organization prevent ransomware attacks.







