The CIS 20 Foundational – Beyond the Basics
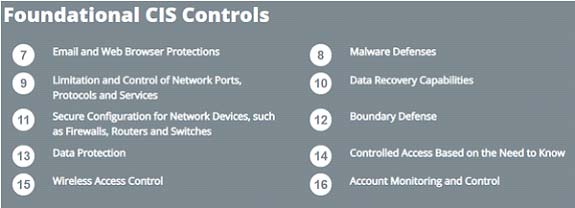
Beyond the Basics — CIS 20 Part Two – Controls 7-16
All organizations need a roadmap for their cybersecurity defense. Piecemeal or fragmented defense strategies, in response to the latest cyberthreat, leave gaps for attacker exploitation. The Center for Internet Security 20 (‘CIS 20’) formerly the SANS 20 is a rigorous set of controls, developed by security professionals and continuously updated in light of new threats and cyber defense enhancements.
We previously discussed the importance of the basic CIS 20 controls (controls 1-6) in How Companies Use CIS 20 to Secure Remote Workers. But they are just the bare minimum. In this article we look at the next step, implementing the CIS 20 ‘foundational’ controls to ensure that your organization is well-protected.
Why go beyond the basic controls?
The basic controls are a great place to start. John Gilligan, The CEO of CIS observed that up to 90 percent of cyberattacks can be prevented by implementing those controls.
Up to 90 per cent of cyberattacks can be prevented by implementing the SIX CIS 20 basic controls!
So, why go any further? Why go beyond the basics? Two important considerations include:
- Many of the foundational controls can be linked back to basic controls, so they don’t necessarily require significantly more work to implement. For example, it is natural to implement CIS 4, ‘Controlled Use of Administrative Privileges’ in conjunction with CIS 14, ‘Controlled Access Based on the Need to Know’
- In order to comply with various data protection laws, such as the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), various cybersecurity controls should be built into your systems to achieve ‘privacy by design’. Implementing CIS 20 foundational controls can go a long way to demonstrating that you are complying with data protection laws.
The foundational controls go beyond the ‘bare minimum’ to ensure that your organization employs a cybersecurity best practice. The diagram below from CIS shows how the different levels of control are categorized.
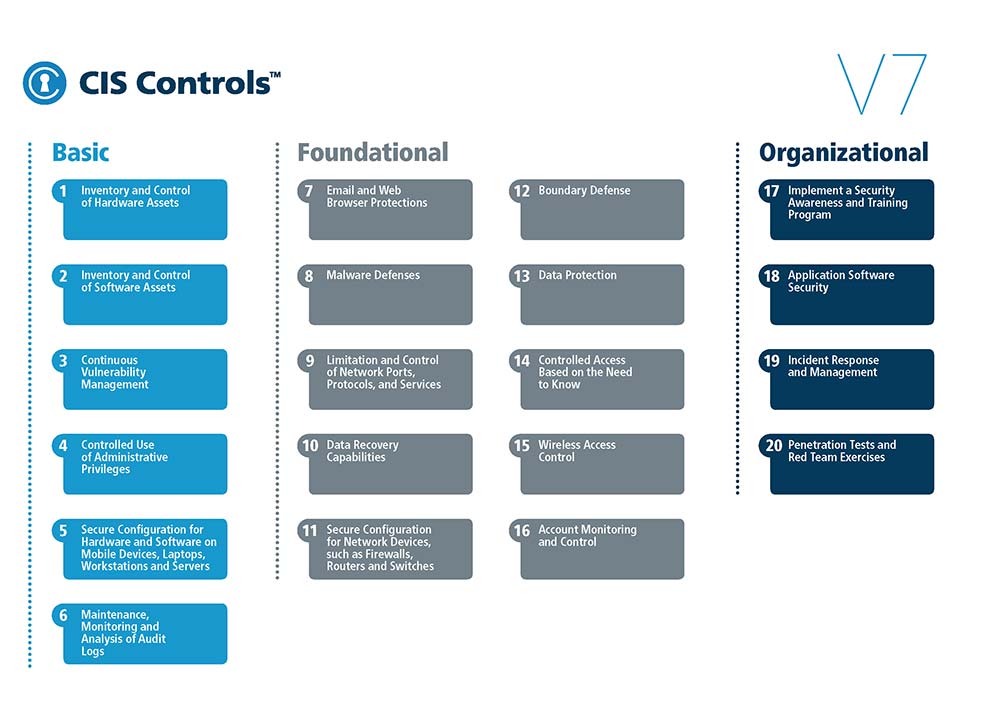
Below we dig into each of the CIS 20 controls 7-16 and suggest steps to take in your organization to comply with these controls.
CIS 7 – Email and Web Browser Protections
A central concept for cybersecurity is minimizing the ‘attack surface’: that is, minimizing the total number of points or gaps where the organization is vulnerable to a cyberattack, or, ‘attack vector’.
The core attack surface in many workplaces is web browsers and email clients: These are the primary gateways for users to engage with untrusted environments. So, what should you do to enhance the security of email clients and web browsers? CIS 7 recommends that you:
- Require that only fully supported web browsers and email clients be used within the organization. The latest available versions of browsers should be used to ensure they incorporate the latest security updates
- Require two-factor identification, complex passwords, spam, and content filters
- Protect against spoofed emails by using Domain-based Message Authentication, Reporting, and Conformance (‘DMARC’). This is a mechanism that checks email authenticity by confirming that the domains of senders align with authorized domains.
CIS 8 – Malware Defenses
This control is about the prevention and rapid response to the deployment of ‘malware’. The sheer number and variety of ways in which malware can infect your system means that organizations need to have an automated detection and response system in place. This should include:
- automated tools for continuous monitoring of all workstations and devices, using anti-virus and anti-spyware, firewalls, and Intrusion Prevention System (‘IPS’) functionality
- automatic verification that each system has received essential updates
- limits on external device use and monitoring of their use
CIS 9 Limitation and Control of Network Ports, Protocols and Services
Just as email clients and web browsers are a key source of security vulnerability, so too are network ports, protocols, and services.
Default settings for servers are not usually configured to maximize the security of the network. This might include automatic enabling of network access, without user or administrator awareness. Attackers are able to scan for, and exploit these servers. The organization needs to respond to this threat by:
- ensuring that only network ports, protocols, and services that serve an essential business function, are enabled
- employing automated port scans on servers to generate alerts that recognize changes from an established baseline
- checking if a server is visible from an untrusted network. If so, and it is not otherwise required for business purposes, move it to an internal Wireless Local Area Network (‘WLAN’)
CIS 10 – Data Recovery Capability
After an incident or outright attack, it can be difficult to know exactly which parts of your information systems have been compromised. This means that robust data recovery mechanisms must be in place. This must include:
- making sure that all data is backed up regularly. The operating system and application software also need to be part of the backup
- testing backup capabilities regularly through data restoration trials
CIS 11 – Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches
As with servers, network devices are not usually configured to maximize system security. All organizations need a process to continuously monitor configurations and the traffic that is permitted to flow through devices. In particular, watch out for exceptions that are applied for business needs, at a particular point in time, that are never corrected. Steps to take include:
- developing a baseline set of configurations, and then documenting any changes against those baselines for specific business purposes
- using automated tools to detect changes to network configurations that can be checked by security personnel
- managing network infrastructure using separate Virtual Local Area Networks (‘VLANs’), or even separate physical connections to ‘segregate’ the activity
CIS 12 – Boundary Defense
Boundary defenses are used to separate and control different networks, with varying degrees of trust. Common boundary defenses include firewalls, web content filtering, routers, and switches. It is recommended that organizations manage this threat by:
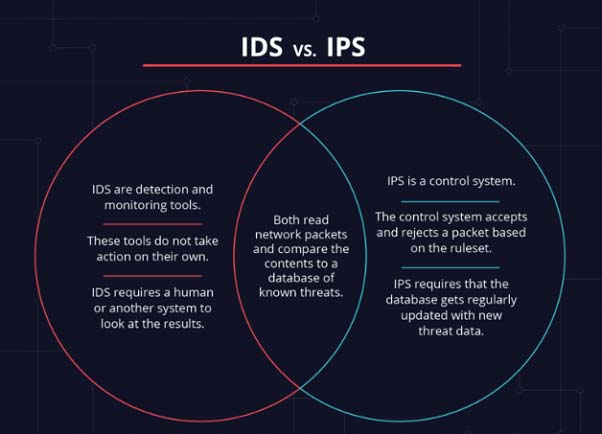
- introducing a multi-layered line of defense, which may include a ‘DMZ’ perimeter network (an effective ‘buffer zone’ between the public internet and a local area network), a network-based IPS, and an Intrusion Detection System (‘IDS’). An IPS and an IDS place ‘sensors’ throughout the system to detect and respond to attacks
- setting up systems to refuse communication with malicious or unused IP addresses, or employ a ‘whitelist’ with permitted addresses only
- controlling the configuration of all enterprise devices remotely logging onto the network.
CIS 13 – Data Protection
We recently looked at the importance of following new personal data protection laws. But all organizations need to take seriously the need to protect all of their data (i.e. not just the personal). This is all the more important, given the continual uptake in cloud solutions. Important mechanisms for protecting data include:
- encryption of important data
- integrity preservation. That is, ensuring that data is valid and won’t be corrupted
- data loss prevention
- automated tools to monitor the network for unauthorized transfer of information, and alerting security professionals
CIS 14 – Controlled Access based on the Need to Know
Organizational assets (e.g., information, systems, and resources), usually have varying levels of sensitivity/importance to the organization. Often, however, organizations do not distinguish between these assets when it comes to access. For example, it is unfortunately very common to store sensitive personal information on the same servers, and with the same security settings, as publicly available information.
The organization should have a classification system for access to critical assets to ensure that only those who require that access, have it.
It is recommended that organizations:
- segment the network based on the classification level of information, locating sensitive information on separate VLANs
- encrypt data when sending sensitive information over low-trust networks
- require detailed audit logging for access to non-public data
CIS 15 – Wireless Access Control
Thefts of data have often occurred through access to organization wireless networks from individuals physically located outside the building. To avoid this, it is recommended that organizations:
- ensure that wireless device connections match an authorized configuration and security profile
- use the Advanced Encryption Standard (AES) to encrypt wireless data
- use a separate wireless network for untrusted devices. This network should have limited access to the enterprise
CIS 16 – Account Monitoring and Control
Organizations need to ensure they take an active role in the status of accounts, their creation, use, and deletion. This reduces the chance that unused/dormant accounts will be exploited by attackers. This can be a major risk with ex-employees or ex-contractors. To deal with this, consider:
- multi-factor authentication for user accounts
- disabling accounts that cannot be connected with a known business process and owner
- establishing a process for immediately disabling accounts on the termination of an employee or contractor
- regularly monitoring all accounts, logging of users after a certain period of inactivity
Conclusion
Building your cybersecurity strategy need not happen all at once. However, once you have the most basic ‘cyber hygiene’ in place by implementing the CIS 20 basic controls (1-6), best practice requires implementing the foundational controls 7-16. Doing this is the best way of ensuring an organization is protected from all of the most common cyber threats.
For recent guidance on implementing cyber hygiene in Windows 10 systems see CIS Controls Microsoft Windows 10 Cyber Hygiene Guide.
To Learn More About How to Protect Your Organization through a Cybersecurity Strategy Please Call Us – as Always We Are Happy to Help – 1 (888) 982-0678