Patch Management Best Practices
Vulnerabilities and Poor Patching Practices Lead to Breaches
In our previous blog posts, which discussed the differences between Vulnerability Scans, Vulnerability Assessments, Vulnerability Management and Penetration Tests we indicated how vital these processes and exercises were to eliminating vulnerabilities quickly and effectively. This year’s breach activity will undoubtedly end at record highs again; the majority of the 5,183 breaches for the first nine months of the year that exposed 7.9 billion records have quite a bit to do with unresolved vulnerabilities.
The remediation gap between when organizations first detect vulnerabilities and when those issues are ultimately resolved is too long and give hackers the opportunity to breach systems and organizations. An Adaptiva survey found that companies overwhelmingly do not have adequate staff to manage the number of vulnerabilities and leveraging current vulnerability management tools is a significant cybersecurity challenge. Further, in a study by the Ponemon Institute, 57% of cyberattack victims stated that applying a patch would have prevented the attack. 34% say they knew about the vulnerability before the attack.
IT Security Teams Struggle with Managing Patching Processes
The gaps between when a vulnerability is in a system or application, then found through scanning or a CVE notice, then fixed, exposes organizations to significant threats. Cyberattackers are increasingly using automated tools to scan systems and often need only a few minutes to breach a system and laterally move throughout the organization to find the data or sensitive records that bring cash on the dark web. Over 15,000 vulnerabilities will be published by the CVE or Common Vulnerabilities and Exposures this year.
That means on average security teams will have to deal with 300 vulnerabilities per week – nearly triple the number of vulnerabilities they had to deal with just 10 years ago. Only about one-third of all the published CVEs are ever seen in a live environment and, of those, only 14% (5% overall) have known exploits against them, however, security teams need to be aware. In addition, with an increasing number of vulnerabilities, applications, systems, cloud issues and so much more it is not surprising that the Adaptiva survey found the following:
- Nearly half (47%) of respondents said scanning endpoints for vulnerabilities was their most challenging security best practice.
- 44% said that the vulnerability scanning tools and solutions are not effective. 44% also suggested that patching applications were challenges.
- 52% of the organizations surveyed suggested that once a vulnerability was detected, it took up to a week to remediate it. 22% require a month or more to fix it, while just 26% can the day they are found.
- Unsurprisingly, 91% of respondents report that maintaining current, compliant security configuration is very or extremely important to their team and the organization.
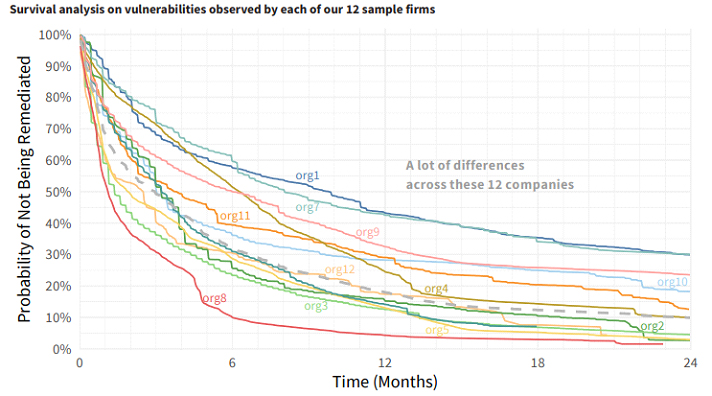
Kenna and Cyentia followed 12 organizations concerning how quickly they patched critical vulnerabilities. As you can see from the chart there is enormous variation between firms. For example, org1 still had 30% of its critical vulnerabilities unresolved after 24 months where org8 has only 10% of its critical vulnerabilities remaining after 6 months. The average survival rate for the 190 million vulnerabilities across the 12 firms after 12 months was 18%, two firms were in the 44% range.
The average time to remediate half of the vulnerabilities was approximately 90 days with the best firm resolving half in 34 days and the worst resolving half in 297 days.
IT Security Staffing Levels Remain Too Low
These problems are compounded as most companies feel a resource crunch. Respondents indicate that they struggle to maintain desired levels of security. Most studies suggest that the shortage of qualified cybersecurity candidates will be approximately 3.4 million unfilled positions by 2021, up from the current level of 2.93 million. 500,000 of the IT security positions will be in North America. Thus, organizations are struggling with current staffing levels as the survey indicates:
- Only 17% of companies believe they are well-staffed and able to do security right.
- Nearly two-thirds (73%) report being understaffed to meet security goals.
- 10% cannot meet high-priority needs and some report an inability to perform essential security operations.
Automation May Help Alleviate the Backlog
Although automated vulnerability scans have posed challenges in terms of the volume of issues they uncover, new options are emerging that leave respondents hopeful for the future. Many reflect the belief that automation can solve a large percentage of their help desk tickets, dramatically reducing workloads.
- 36% of respondents indicate that over half of their help desk tickets can be automated.
- Another 33% think they could automate more than one quarter.
- Automation opportunities include break/fix software tickets which represent 28% of requests, and application installations or upgrades, which account for 14% of tickets.
8 Patch Management Best Practices
A team of researchers from Cyentia, Virginia Tech, and the RAND Corporation presented a white paper titled Improving Vulnerability Remediation Through Better Exploit Prediction they found that the 4,183 security flaws that had been exploited between 2009 and 2018 were a small percentage of the total of 76,000 of all vulnerabilities discovered during that time.
They further suggested that while that works out to be about 5.5% of vulnerabilities being exploited in the wild, one in 20 vulnerabilities being exploited is quite a lot more than the one in 100 shown in several prior studies that minimized the impact of most vulnerabilities.
- Patch the highest risk applications first
- In some years, a single unpatched application like Sun Java was responsible for 90% of all cybersecurity incidents
- Prioritize patches by criticality
- Most organizations apply patches using a date approach rather than a risk-based approach
- Prioritize vulnerabilities by CVSS Score
- a CVSS base score of 0.0-3.9 is considered “Low” severity; a base CVSS score of 4.0-6.9 is “Medium” severity; and a base score of 7.0-10.0 is “High” severity
- Prioritize systems by criticality
- Systems that house critical data or business processes should be prioritized over low priority systems
- Test patches prior to rolling out everywhere
- Some patches will break applications – again, Java was well-known for this
- Consolidate software versions
- For example, choose one version of Windows, Linux, or macOS to simplify patching
- Forget about Zero-Day Exploits and prioritize patching
- The percentages suggest that these are still low probability security issues versus known vulnerabilities in terms of what will be exploited by a hacker
CVE Enrichment Projects
As a final note, CVE information is a critical element of any patch management solution. Most research indicates the scoring is improving and related organizations are adding vendors and other information that will make patch management processes easier and more effective.
In addition to the basic CVE information produced by MITRE, other research leverages the details added to each CVE by the National Vulnerability Database (NVD). NVD enriches the base CVE information with details leveraging other community projects, which include the following:
- Common Vulnerability Scoring System (CVSS). This provides a process to capture the principal characteristics of a vulnerability and produce a numerical score that reflects its severity. The CVSS standard has very recently moved to version 3, but most published CVEs were recorded using version 2, so we use version 2 in this report. CVSS was developed and is maintained by the Forum of Incident Response and Security Teams (FIRST).
- Common Platform Enumeration (CPE). This provides a standard machine-readable format for encoding names of IT products, platforms, and vendors. It was developed at MITRE, but ongoing development and maintenance is now handled by NIST.
- Common Weakness Enumeration (CWE). This provides a common language for describing software security weaknesses in architecture, design, or code. It was developed and is maintained by MITRE.
Each piece of enrichment data offers a potentially useful context for decisions. Basic remediation strategies may rely on CVSS alone, while others will factor in the type of vulnerability (CWE) along with the vendor and product and the exposure of the vulnerabilities across environments.







