ZeroLogon Illustrates the Importance of Vulnerability Management
ZeroLogon and the Importance of Vulnerability Management
In this blog, we have written about regular security hygiene including executing regular vulnerability assessments and implementing a viable vulnerability management program. However, many security professionals see vulnerability management as a cumbersome set of tasks usually comprised of simple scan and patch cycles; ZeroLogon is an excellent example of why vulnerability management is so critical.
The ZeroLogon vulnerability allows a hacker to take control of a domain controller (DC), including the root DC. This is done by changing or removing the password for a service account on the controller. The hacker can then simply cause a denial of service or take over and own the entire network.
U.S. Department of Homeland Security issued an emergency directive instructing all federal agencies to patch the vulnerability by the end of last month. DHS’s Cybersecurity and Infrastructure Agency (CISA) said in the directive that it expected imminent exploitation of the flaw — CVE-2020-1472 and dubbed “ZeroLogon” — because exploit code which can be used to take advantage of it was circulating online.
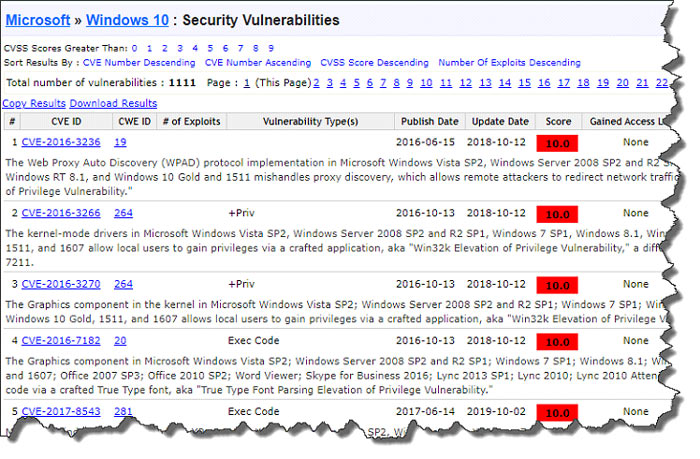
The CVE Score of the ZeroLogon vulnerability is a 10. This year, among the 20,000 vulnerabilities that will likely be reported – which is again a record over last year; only 30 or so will rank as a 10 in criticality.
Windows ZeroLogon EP (ZEP) is a vulnerability in the Netlogon protocol used by Windows Server. Secura’s security expert Tom Tervoort discovered the vulnerability and explained how the flaw in Microsoft’s software would allow hackers to do significant damage. “The vulnerability is an easy exploit for attackers to deploy and will surely cause problems for organizations who have not yet patched their ActiveDirectory systems.” Tervoort, an independent security researcher reported the vulnerability to Microsoft and documented its danger in his blog. 60 days ago, in the set of Windows updates, a patch was included that solved the immediate problem, however, for organizations that used older versions of Netlogon, the patch did not solve the entire problem.
This is why vulnerability management and more specifically patch management is so difficult, yet so critical.
Last month, Microsoft officially announced the existence of the vulnerability. Since then, it has been used by a number of cybercrime groups as part of their attacks. We have observed attacks where public exploits have been incorporated into attacker playbooks,” Microsoft said. “We strongly recommend customers to immediately apply security updates.”
Microsoft released a patch for the vulnerability last month, however, as we suggested in previous posts about patch management, it is not uncommon for businesses to delay deploying updates for days or weeks while testing to ensure the fixes do not interfere with or disrupt specific applications and software.
But the average time from patch release to deployment is still too long. Researchers state that in the average organization, it takes between 60 to 150 days (about 5 months) after a patch is released to be finally installed. This is known as the Mean Time to Patch (MTTP).
CVE-2020-1472 earned Microsoft’s most dire “critical” severity rating along with the CVE; in this case meaning attackers can exploit it with little or no help from users. The flaw is present in most supported versions of Windows Server, from Server 2008 through Server 2019.
Figure 1 – CVE Vulnerability List of Windows 10 Vulnerabilities
How Does ZeroLogon Work?
ZeroLogon is caused by a flaw in the implementation of the cryptographic algorithms in Netlogon. It enables an unauthenticated user to falsely authenticate to the system and can be used to gain Domain Administrator privileges on a network.
Netlogon has a multi-stage authentication process designed to create a shared session key between the client and the server:
- The server and client each generate an eight-byte challenge and send it to the other
- Hash the domain password (known to both the client and server) using MD4
- Concatenate the two challenges to this value and hash with SHA256
- Use the first 16 bytes of the result as the session key
To verify that the client and server have generated the same session key, the client encrypts the eight-byte challenge that they generated using it. This is sent to the server, which decrypts and verifies it.
This authentication process is not a problem with ZeroLogon. The issue arises with how Microsoft implemented the encryption in ZeroLogon.
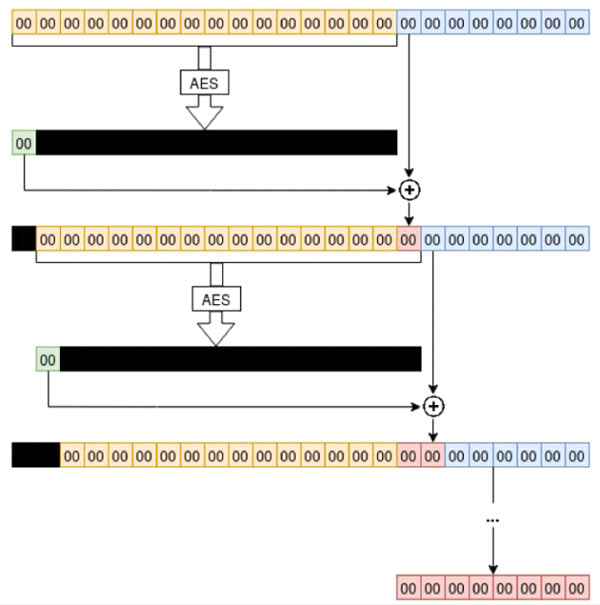
Image from https://www.secura.com/pathtoimg.php?id=2055
Cipher Feedback (CFB) mode is a common block cipher mode of operation used to define how messages longer than a standard block (128 bits in AES) should be encrypted. Instead of using the full 18-bit version, Microsoft defined a custom version (CFB8) that encrypts data one byte at a time (as shown above).
Additionally, Microsoft made the mistake of setting the initialization vector (IV) to be always zero when it should be random. Combined with the use of CFB8, this means that, if encryption of a plaintext starting with a zero byte produces a ciphertext starting with a zero byte, an all-zero plaintext will encrypt to an all-zero ciphertext.
In the case where the encryption algorithm will “stick” like this (which happens with 1/256 probability), an attacker can successfully encrypt an all-zero plaintext without knowledge of the encryption key. This creates two major problems for Netlogon:
- False Authentication: A Netlogon authentication process is successful if the client can successfully encrypt the eight-byte challenge that it generated. By using an all-zero challenge, an attacker can do this by sending an all-zero ciphertext to the server. This means that the attacker doesn’t need to know the domain password to authenticate to a domain controller.
- Server Password Reset: Once authenticated, a user can call a function to change the password of the server, which takes an encrypted set of inputs. For this function, a set of all-zero inputs will set the password to an empty password (due to another design error). This gives the attacker access to the server itself.
In combination, these two factors can give an attacker full access to and control over a domain controller. This may provide full access to an organization’s entire network.
The Impact of ZeroLogon
ZeroLogon is an authentication bypass for Netlogon, a system used for communication with network domain controllers. An unauthenticated user with access to the domain controller can exploit the vulnerability, enabling them to have a number of different impacts on an organization’s network and cybersecurity:
- Initial Network Access: The Netlogon vulnerability does not require the user to have authenticated access to the domain controller. If an attacker can exploit the vulnerability, it provides them an initial foothold within an organization’s network.
- Compromised Credentials: After authenticating to the domain controller, an attacker can call functions that dump the complete list of password hashes that it contains. These hashes can be cracked offline to gain access to user accounts and for use in credential stuffing attacks.
- Full Network Takeover: By exploiting the Netlogon vulnerabilities, an attacker can reset the password on a domain controller. This enables them to gain Domain Administrator access and full control over the associated network.
- Denial of Service Attack: The process that gives an attacker full Domain Administrator access places the domain controller in an unstable state. If the server is restarted, it can break services reliant upon the domain controller.
Why Prompt Patching is Essential
The ZeroLogon vulnerability was publicly announced last month. However, a patch for it was included in the August 2020 batch of Windows updates. This provided organizations with ample time to test and apply these patches to vulnerable systems.
However, many organizations have not applied the patch, and the vulnerability is being actively exploited by cybercriminal groups. Microsoft issued a warning stating that the Iranian MuddyWater advanced persistent threat (APT) group is actively using the exploit in their attack campaigns. As the exploit provides complete control over the network managed by a domain controller, this has a significant impact on an organization’s cybersecurity.
Dustin Childs, communications manager for Trend Micro’s ZDI, says there is nothing theoretical about the bug or how it can be exploited. “This vulnerability could allow unauthenticated attackers to run arbitrary code on affected Windows domain controllers,” he says.
The code would execute with elevated privileges and allow an attacker to completely take over the domain controller and, from there, essentially the entire domain.” Failure to patch means you are leaving one of your most critical assets unprotected from an active threat,” Childs says. “This is not a theoretical bug that may be exploited by sophisticated attackers. This is a bug being actively used by threat actors against enterprises.”
Patch management can be a challenge due to the sheer number of new vulnerabilities that are discovered and publicly disclosed each year. However, it is essential that organizations patch high impact vulnerabilities as quickly as possible to avoid exploitation. In the case of ZeroLogon, which again has a CVSS base score of 10, meaning the vulnerability has received the highest possible impact rating. This is what prompted the Cybersecurity and Infrastructure Security Agency (CISA) to issue an emergency directive to US government organizations that the vulnerability must be patched on all systems within 8 days.
The Importance of a Robust Vulnerability Management Strategy
ZeroLogon is a single vulnerability that can completely destroy an organization’s network security. However, it is only one of tens of thousands of vulnerabilities that are discovered each year.
While these vulnerabilities pose varying levels of threats, it is important to have the ability to make informed decisions about potential risks and to be able to respond effectively. This requires an organization to have a robust vulnerability management program in place with the associated policies, processes, and procedures for rapidly deploying patches throughout the organization.