The 4 Key Benefits of Micro-Segmentation
Getting Started with Micro-segmentation
Written by Javier Hernandez, Senior Security Architect @ SecureOps
What is Micro-Segmentation
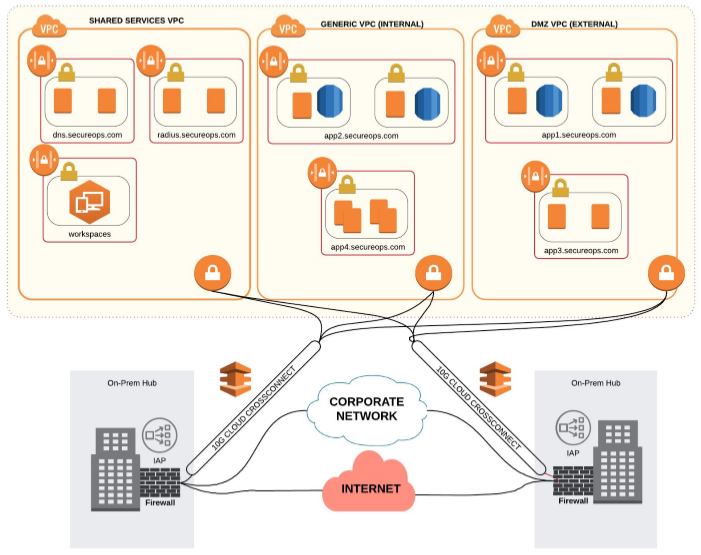
Micro-segmentation is an emerging security best practice that offers a number of advantages over more established approaches like network segmentation and application segmentation. It has emerged as a network security technique that enables security architects to segment the data center into separate security segments through to each individual workload level. Security teams can then establish controls and deliver services for each unique segment of the infrastructure.
An enormous cost/benefit is that micro-segmentation enables info sec teams to deploy nearly custom security policies inside a data center using network virtualization technology instead of installing multiple physical firewalls. In addition, micro-segmentation can be used to protect every virtual machine in an enterprise network with policy-driven, application-level security controls. Because security policies are applied at a application level, micro-segmentation tactics can significantly increase an organization’s security defense.
Micro-Segmentation and The Cloud
Micro-segmentation offers added granularity at a time when many organizations are adopting cloud services and new deployment options like containers that decrease the reliance and effectiveness of traditional perimeter security life antivirus and firewalls.
Infrastructure visualization plays a critical role in the foundation of a sensible micro-segmentation strategy. Visualization makes both activity in the IT environment easier for security teams to understand.
This improved visibility allows security teams to define micro-segmentation policies that will alert on and block suspicious activity. Micro-segmentation policies can take many forms, including controls based on environment type, regulatory scope, application, and infrastructure. Micro-segmentation will also allow security teams to apply the principle of least privilege system access more extensively throughout cloud environments. This, as we know will provide a far more effective security defense posture than traditional network controls.
Micro-segmentation strategies need to be consistent across cloud providers. By separating security from the cloud provider, companies can avoid being locked in to a single cloud provider which will prevent them from driving provider costs up; in addition, they will and avoid infrastructure complexity if a merger or acquisition creates mixed cloud environments.
Micro-segmentation is a new concept to many, but it has emerged as an important tool for IT security teams who are tasked with maintaining security policies and compliance as they move to cloud and hybrid cloud environments.
Benefits of Micro-Segmentation
Micro-segmentation is a method of creating secure zones in data centers and cloud deployments that allow companies to separate workloads and secure them individually. Among other benefits, micro-segmentation makes network security more granular and thus more effective.
As IT infrastructure becomes more dynamic and cloud infrastructure and containers assume more important roles, the effectiveness of traditional perimeter security is diminished. Instead, IT teams are forced to enhance their ability to detect and prevent suspicious lateral movement among heterogeneous data center and cloud systems and assets. Micro-segmentation provides several key benefits to organizations facing this challenge.
1. Reduce Attack Surface
The rapid transition from traditional on-prem data centers to cloud and hybrid cloud models has delivered cost and convenience benefits, it has also increased the size of the organization’s attack surface that security teams are forced to defend. In addition, this challenge is increased by the infrastructure change and the emerging application deployment models that organizations have adopted.
Many existing security techniques that help reduce the attack surface, such as system hardening, vulnerability management practices, access controls, and network segmentation, remain best practices even as cloud usage grows. However, security teams seeking to reduce their organization’s attack surface can benefit from greater visibility and more granular policy controls that can be applied consistently from their on-prem data center to the cloud.
Having the ability to visualize the attack surface makes it much easier to design tactics to reduce its size. This perspective can then be used to develop micro-segmentation security policies that govern application activity with increased granularity. Controlling application activity makes it possible to design security policies with application logic in mind and implement a zero-trust environment where only approved application activity can execute.
As organizations continue to move to hybrid cloud environments, many overlook the increase in the size of their attack surface. The new physical environments, platforms, and application deployment methods create security gaps. To effectively reduce the attack surface in hybrid cloud environments, a micro-segmentation solution must employ new policies that are consistent across a variety of data center and cloud environments as well as a mix of operating systems and application deployment models.
2. Improve Lateral Movement Security
For years, security teams have focused on perimeter protection, however lateral or east-west traffic is outpacing north-south traffic in both volume and significance to the security team. This is driven by such factors as changes in data center scaling strategies, big data, and the use of cloud services. It has become critical for IT security teams to develop capabilities to prevent unwanted lateral movement of suspicious data in these new environments.
Lateral movement is the subsequent actions that attackers who have gained access to an IT network take to move from system to system to find their target data. Lateral movement of data is difficult to detect because it blends in with the massive volume of ordinary east-west traffic in the environment.
3. Secure Critical Applications
Implementing a sound micro-segmentation strategy will allow security teams to gain greater infrastructure visibility and secure critical applications. The 3 proven benefits micro-segmentation provide in order to help secure critical applications include:
- Provides consistent security across different platforms
- Delivering process-level granularity that helps align security policies with application logic
- Enabling security policies to be implemented in the data center and the cloud consistently
Micro-segmentation provides both power and flexibility which empowers organizations who must protect high-value targets like domain controllers, privileged access management systems, and jump servers. In addition, as we suggestion in the cloud section above, it also valuable as organizations transition to cloud services and new application deployment approaches like containers.
Micro-segmentation can also play an important role in securing industry-specific applications and data including healthcare applications, financial services applications that are subject to PCI DSS and other regulations and legal applications with privacy concerns. Micro-segmentation provides granularity which makes it easier to create boundaries around sensitive data across multiple environments and platforms for security defense and to simplify the audit process.
4. Improves Regulatory Compliance Posture
A fourth key benefit of micro-segmentation is that it helps organizations improve their regulatory compliance posture. Segments of the IT infrastructure containing regulated data can be isolated and thus, compliant usage can be better enforced.
One of the challenges of achieving PCI cloud security compliance, for example, is proving that systems marked as out of scope are really separate from the cardholder data. Micro-segmentation tools with sophisticated labeling functionality will allow you to examine the PCI environment and examine the flow of data and communication in more granular detail. The ability to drill down to examine specific protocols at the process level provides unprecedented levels of control for compliance.
Final Words of Advice
Start with a Phased Approach
A common misconception is that micro-segmentation is an “all or nothing” proposition that requires a substantial commitment of staff and resources, conceivably over years, without a clear idea of what a successful outcome looks like. Start by focusing on projects that are manageable, fairly easy to complete, and can deliver tangible results. Prioritize systems that hold PII or other critical data.
Implement a Zero Trust Approach
The Zero Trust architecture approach, initially introduced by Forrester Research, promotes “never trust, always verify” as its foundational principle. With Zero Trust there is literally no default trust built-in for any entity — including users, devices, applications, and packets. Palo Alto Networks provides proven hardware-based segmentation often geared to large organizations while Sophos delivers world-class endpoint technology often suited to SMB organizations.
Create a Map to Establish Barriers and Monitor
ESG analyst Jon Oltsik last year reported that 68% of enterprises are using some form of software-based micro-segmentation technology to limit lateral exploration of networks by hackers and make it easier to protect their applications and data.
Create a complete map that identifies the flows, servers and security devices within the data center that your business applications rely on to function correctly. Once the map is outlined you can then choose the best places on the data center network to place the security filters (such as virtual firewalls or other security controls) and create secure borders between segments.
Conclusion
As we suggested in our 4 major benefits in this blog post, Micro-segmentation will ultimately:
- Reduce the attack surface
- Improve breach containment through limiting lateral movement and providing greater visibility to and consistent security policy to critical application
- Improve regulatory compliance posture
The benefits of micro-segmentation are maximized when the approach is integrated with an organization’s broader infrastructure, such as orchestration tools. It’s also essential to select a micro-segmentation approach that works across physical servers, virtual machines, and multiple cloud providers for maximum effectiveness and flexibility.
Security experts and analysts cite micro-segmentation as an evolving best-practice solution for securing data center assets and implementing a “zero trust” security model. Micro-segmentation involves setting granular security policies around individual or logically grouped applications. Those policies dictate which applications can and cannot communicate with each other; any unauthorized communication attempt is not only blocked but also triggers an alert that an intruder may be present.