How to Improve Your SOCs Effectiveness – Part 1
How to Improve Security Operation Center (SOC) Effectiveness – Part 1
So many articles and blog posts have been written on SOCs, how they are structured, what their mission and purpose is, and of course how to improve their effectiveness. I wanted to tackle this subject because there is so much good thinking out there, but the recommendations and ideas are difficult to implement, contrast with one another, and are sometimes even difficult to even understand. The goal here will be to start with the fundamentals then move into what we think are actionable recommendations to improve how your SOC performs.
In a previous blog post, we addressed “How to Improve Your Security Operations Center” which provides a good foundation for what we will discuss in the post. This post will be deeper and provide much more detailed information, however.
What is a Security Operations Center?
Let’s start with what a Security Operations Center and how it executes a Computer Defense Network (CDN) strategy given the evolution of hackers, cyber-attacks and malware since the true birth of the current SOC in the 1990s.
Principally, a Security Operation Center (SOC) is a centralized function within a company that leverages IT security people, processes, and technology to monitor and improve an organization’s security while preventing, detecting, analyzing, and responding to cybersecurity incidents.
Today’s SOC is essentially the hub that collects log data from across an organization’s IT infrastructure, including its networks, devices, appliances, and databases and other IT assets across geographies. The increase of advanced threats makes collecting data from diverse sources critical, as each piece of data may provide insight into malicious behavior on the network.
Here is the real issue we’ll be addressing in this post – most SOCs, unfortunately, have difficulty keeping cybercriminals—even the unsophisticated ones—out of the organization. SOC analysts and other IT Security professionals are defending against sophisticated and constantly evolving malware, nation-states with hundreds of hackers, insider threats and worst of all, poorly trained employees who fall prey to phishing attacks.
As we consistently hear in the IT security industry, criminals need to find only one way in while the good guys in the SOC must defend countless ways in, limit damage, and most difficult of all, find and remove the malware or malicious code that infiltrated the systems.
“An attacker only needs to be right once, an analyst and their tools must be right thousands of times” – Quoted by anyone and everyone in an SOC ever.
Defining a Security Operation Center
Fundamentally, the responsibility of the SOC is to defend against unauthorized activity within computer networks, including monitoring, detection, analysis (such as trend and pattern analysis), and response and remediation responsibilities. The SOC, folks in the SOC – particularly incident response professionals and teams have been given a variety of titles and acronyms so let’s list them out and discuss them as we go forward. They include:
- Security Operations Center (SOC)
- Cybersecurity Operations Center (CSOC)
- Computer Security Incident Response Team (CSIRT)
- Computer Incident Response Team (CIRT)
- Computer Incident Response Center (CIRC)
- Computer Security Incident Response Center (CSIRC)
- Computer Emergency Response Team (CERT)
The SOC is usually led by a SOC manager/chief and may include incident responders which we listed above, SOC Analysts (levels 1, 2 and 3), threat hunters and incident response managers. The SOC reports to the CISO, who in turn reports to either the CIO or directly to the CEO.
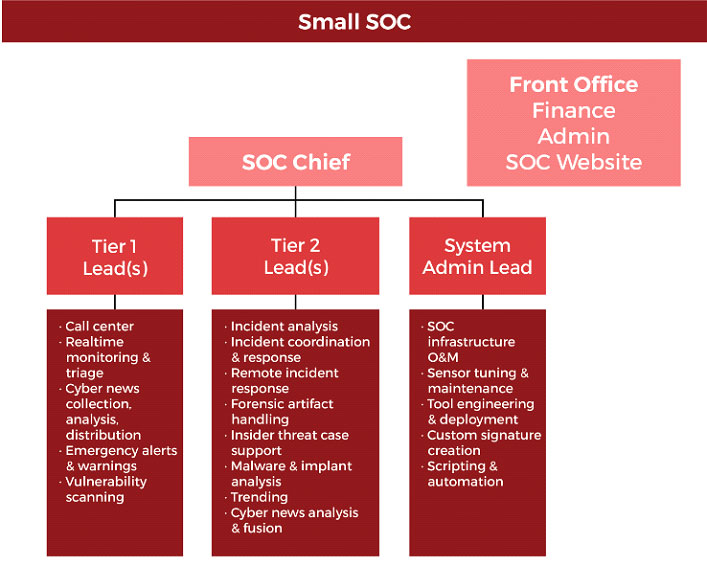
SOCs are constantly evolving to deal with changes including principally:
- The rise of advanced persistent threat (APT’s) and the evolution in the cybercriminal’s tactics, techniques, and procedures (TTPs)
- The organization’s shift to IT consolidation and the cloud
- The massive growth of mobile and BYOD which blur the defense borders for the IT security organization
- The transition from the cybercriminals use of network-based buffer overflow attacks to client-side attacks or website attacks
- The lack of qualified personnel and often budget for the SOC to meet achieve its mission
Today, SOCs are built around a hub-and-spoke architecture, where Security Information and Event Management (SIEM) technology aggregates and correlates log and other data from assets and threat intelligence feeds. The spokes of this model often include a variety of types of technology and systems including, such as vulnerability scanning and assessment solutions, governance, risk and compliance (GRC) systems, application and database scanners, intrusion detection and prevention systems (IDS/IPS), firewalls or next-gen firewalls (NGFW), user and entity behavior analytics (UEBA), endpoint detection and remediation (EDR), and threat intelligence platforms (TIP).
What are the Day to Day Responsibilities of an SOC?
A typical SOC’s responsibilities include the following tasks or elements:
- Operating the security technologies, we listed above which include SIEM’s, IDS/IPS, EDR, TIP’s, and lots of other new security technology that organizations want to purchase to supplement their people and processes (many of the top security pro’s estimate that >50% of these technologies DO NOT reduce the chance of a breach)
- Prevention of cybersecurity incidents through proactive:
- Continuous threat analysis
- Network and host scanning for system and software vulnerabilities
- Countermeasure deployment coordination
- Security policy and architecture consulting
- Monitoring, detection, and analysis of potential intrusions in real-time using historical baselining and trending on security log and other security data
- Incident response through coordinating resources and directing the use of timely and appropriate countermeasures
- Providing situational awareness and reporting on cybersecurity status, incidents, and trends in adversary behavior to appropriate organizations
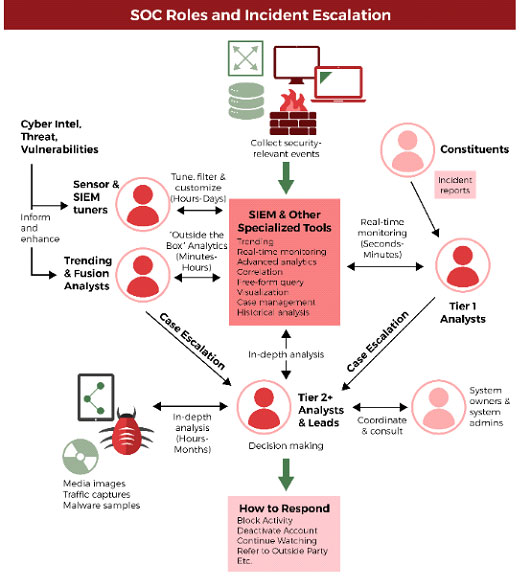
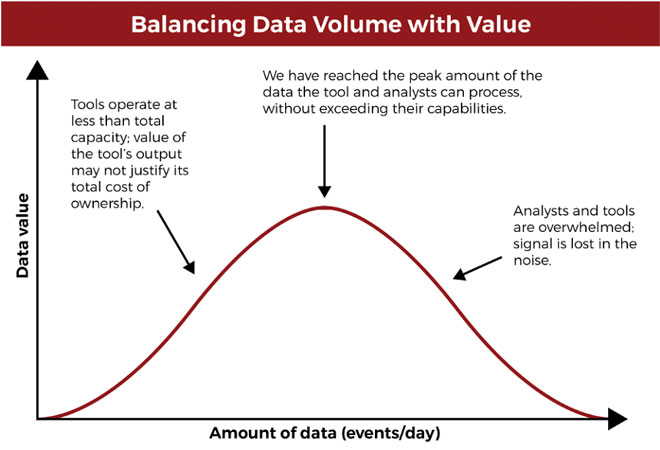
Of these responsibilities, the most time-consuming is the collection, normalization, and analysis of log and other data. Security logs, threat intelligence feeds, and other security-related data often overwhelm the analysts in the SOC with collecting, analyzing, and archiving tens or hundreds of millions of security events per day. In addition, Firewalls, IDS/IPS and SIEM’s are noisy, meaning they are constantly alerting analysts of security events which analysts must investigate to rule out an incident.
Let’s clarify that last statement because it is one of the most significant problems for Tier 1 and 2 analysts. There are thousands of events that analysts must spend time investigating for every legitimate incident. Further, an actual data breach is a type of security incident. All data breaches are security incidents, but not all security incidents are data breaches. Data breaches are typically a loss or exposure of sensitive data. Thus, the progression is an event, incident, breach – for every breach there are typically hundreds of incidents and for every incident, there are thousands of events. This is one of the major issues for most if not all SOCs.
The progression for analysts is event, incident, breach – for every breach there are typically hundreds of incidents and for every incident, there are thousands of events. This is one of the major issues for most if not all SOCs
How SOC Analysts Respond to Incidents
In this section, we’ll simply set up how SOC’s and incident response team often respond to incidents. In part 2 we’ll use that information to figure out how to improve the incident response process as well as other processes in the SOC. We’ll try and be as brief and straightforward as possible; as you all know this could be an entire incident response policy, sandbox, reverse engineering, forensics discussion and we want to stay on point.
Ok, let’s say the SIEM fires off an alert that someone is trying to access a system or application that they shouldn’t be accessing. At that point, the alert becomes an event. The SOC analyst will investigate the event and try and understand if the act was malicious or not. If the analyst thinks that the IP address is suspicious, or they believe they may be under attack from malware on the system will likely escalate the incident to a higher tier analyst or the incident response team.
Now, as we said earlier, SOC’s investigate lots of incidents so they don’t want to initiate countermeasures immediately because there are usually negative consequences to countermeasures including:
- If the SOC blocks benign activity thinking they are blocking an attack it may impact legitimate business
- There are thousands of attacks per day, SOCs do not want to overreact to an attack and lose forensic evidence by disconnecting communication or shutting down target equipment
- If the SOC deploys certain countermeasures they may alert the attacker who will then try and cover their tracks and the SOC have a more difficult time understanding the extent and severity of the attack; or if the attack is ongoing in other systems in the environment.
- A response action could impact an organization’s mission more than the incident itself
Further, there are a variety of attacks so analysts will need to gather basic information like suspicious entries in system or network, excessive login attempts, unexplained new user accounts, unexpected new files, etc., in order to narrow down the possibilities and start limiting the scope of the attack.
Understanding the extent and severity of the intrusion by watching the adversary is sometimes more effective than performing static forensic analysis on compromised systems, once the adversary is no longer present.
Preparing for How to Improve SOC Effectiveness – Part 2
So, we defined an SOC and the players within the organization, discussed their responsibilities, identified several problems that SOCs face almost universally and discussed how they often deal with an event, incident, attack, and breach. In part 2 we’ll dig into how high-performing SOCs have dealt with their issues and developed solutions.
To Learn More About How to Empower Your Security Analysts and Managed Your Security Technology including SIEMs and Firewalls please call us – as Always We Are Happy to Help 1 (888) 982-0678