Implementing Vulnerability Management Programs is Still Challenging for Many Companies – Part 1
We’ve written considerably on Vulnerability Management, Vulnerability Assessments, and Patch Management because they are critical to preventing cyber attacks. I’ve provided links to several of the most-read blog posts we
Protecting and Responding to Ransomware Attacks – A Best Practice
Let’s start with the basics: ransomware, a malicious software, poses a significant threat to organizations by encrypting their data and demanding payment for its restoration. This type of attack disrupts
The Indigo Bookstore Ransom Cyber Attack – Lessons Learned
The recent attack on the Indigo Bookstore left many cyber security analysts scratching their heads. How did attackers seize control of systems through ransomware, and how was a zero-day exploit
CISO’s Earning a Seat at the Board is Now a Priority
Our crack team here at SecureOps found one of the more interesting studies concerning the of focus both Boards of Directors and senior executives are giving their organization’s cybersecurity investments and strategy. Skybox Security was commissioned to perform a study of executives across a variety of industries which found that 27% of executives say new technologies are their largest cybersecurity worry. In our new environment of slower growth, higher interest rates and rampant inflation, business growth is a top priority. Despite the environment, most organizations are still smack dab in the middle of a digital transformation putting cybersecurity leaders in the position of having to secure new technologies like cloud, IoT, BYOD and countless other technologies with little or no budget increase. These digital transformation investments and strategies including investment into new markets, and global expansion bring a level of risk for organizations with the expectation of new revenues and growth. The Skybox Security study showed cybersecurity is now at a critical inflection point:
- Global business leaders agreed we have entered a new era of cyber risk. In 2021, the number of material breaches jumped 24.5%.
- 27% of executives believed their organizations were not well prepared for today’s rapidly changing threat landscape.
- And 41% of executives noted that “cyber risk initiatives have not kept pace with digital transformation,” with 39% of CEOs saying they have “inadequate budgets to ensure cybersecurity.”
Factoring in Risk into Organization Growth Models
Cybersecurity readiness is a choice, and CISOs can use outcome-driven cybersecurity metrics and cyber risk scores to paint a clear picture of prevention investments. Many organizations now develop risk models when creating their digital strategies. Cybersecurity risks and attacks ultimately impact forecasted financial expectations. Considering all the variable factors within cybersecurity incidents, including malware - particularly ransomware attacks, loss of data, and the impact on the organization's brand, including the loss of trust among customers, investors, and business partners, how can an organization develop a predictable model for risk? A corporate-wide security posture risk-based approach considers two critical tasks. (1) it designates security as the primary goal. This enables the organization's leadership to prioritize investments, such as cybersecurity training and incident response. (2) the approach distills top-level objectives into practical implementations that align with the boardroom priorities.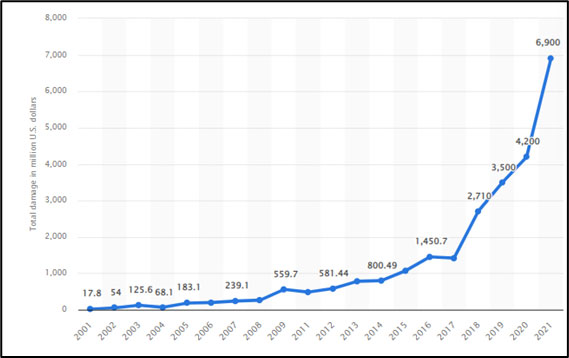 Companies have adopted various approaches to reducing cyber risks and their potential impact. Some have focused on improving existing processes and procedures through risk assessments; others have sought to improve technology and information systems. However, regardless of how they've approached the problem, most have found that the best way to reduce cyber risk is to adopt a systematic, disciplined process that focuses on identifying and prioritizing threats, then defending against them. In doing so, companies can significantly reduce costs and increase efficiency. They can also avoid wasting money on unnecessary investments and controls in order to spend more wisely on the investments and activities that will ultimately reduce risk. Many of these investments include preventing a loss of data confidentiality from insider threats and breaches.
Companies have adopted various approaches to reducing cyber risks and their potential impact. Some have focused on improving existing processes and procedures through risk assessments; others have sought to improve technology and information systems. However, regardless of how they've approached the problem, most have found that the best way to reduce cyber risk is to adopt a systematic, disciplined process that focuses on identifying and prioritizing threats, then defending against them. In doing so, companies can significantly reduce costs and increase efficiency. They can also avoid wasting money on unnecessary investments and controls in order to spend more wisely on the investments and activities that will ultimately reduce risk. Many of these investments include preventing a loss of data confidentiality from insider threats and breaches.
Cybersecurity Strategies Developed Inside the Boardroom
Cybersecurity roles, including the chief information security officer (CISO), have a powerful presence within the executive C-suite within the organization…finally. No longer considered just an expense item, cybersecurity has several businesses benefits, including:- Revenue protection
- Brand protection
- Reduction of overall risk to the business
- Increase in the enterprise value of the organization
- The ability to open new markets domestically and globally
Revenue Protection
Sound and effective cybersecurity risk management and proven defense effectiveness adds a vital element of trust across customers and employees. Customers who trust their providers with their information, including their approach to safeguarding their private information do more business those organizations.Brand Protection
Brand protection also benefits from improvement cybersecurity investment. Organizations with no reported public or private data breaches, no failures to meet privacy and compliance frameworks, and a proven governance capability embedded into cybersecurity in their culture are more likely to increase brand equity. This culture originates from the board of director’s investment, acceptance, and leadership in having cybersecurity initiatives placed on par with growth initiatives.Reduction of Risk
Risk and security incidents continue to rise in large part because of human error and employee negligence. Email phishing attacks continue to impact organizations negatively. Organizations realize cybersecurity is not isolated to one area. A breach can occur across all areas of the organization including 3rd party partners. Adopting a corporate-wide cybersecurity frameworks including NIST, CIS 20, or ISO 27001 help create a unified enterprise-risk reduction and cybersecurity capability.Increasing Organization Equity
Many organizations often will rely on cyber insurance to help offset the expense of financial damage from cyber-attacks. Many external audit findings find that cybersecurity insurance is an immediate necessity to the business; however, they also recognize this financial protection is not a long-term strategy, but simply a way to reduce the overall cost of a damaging attack. Unfortunately, insurers have found that the loss ratio in cyber insurance has been nearly 110% in many cases and premiums have skyrocketed.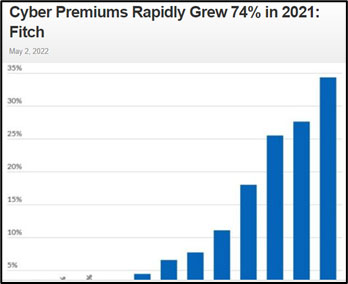 The cost of cybersecurity premiums continues to rise along with demand for more significant layers of cybersecurity solutions, keeping experienced cybersecurity professional security teams hunting for new technology. The organization must develop and enforce security policies, effective security operations (SecOps) capabilities, and capacity to meet the constant security attacks against organizational assets.
The cost of cybersecurity premiums continues to rise along with demand for more significant layers of cybersecurity solutions, keeping experienced cybersecurity professional security teams hunting for new technology. The organization must develop and enforce security policies, effective security operations (SecOps) capabilities, and capacity to meet the constant security attacks against organizational assets.
Equity Gain
Cybersecurity support, revenue gain, and governance positively affect the organization's stock price, enterprise value, and business operations. Organizations who successfully mitigate attacks against their organization by employing a risk-based cyber strategy continue to be effective. Organizations that suffer from security breaches will lose favor with current and future investors. Several organizations continue to partner with global IT firms to help with the architecture, deployment, and optimize their blockchain platforms, partially due to the lack of available talent to address cybersecurity concerns.Protecting Global Expansion
Digital transformation strategies, including expanding globally into new markets with new products, adds additional risk and potential cybersecurity concerns across the organization’s attack surface. Organizations with a proven well-executed cybersecurity strategies help improve the chance of effectiveness as they venture into new global markets. Organizations that invest in cyber security adaptive controls and cyber resilience to protect against attacks, damage and downtime are more successful in their digital transformation strategy. Talented, experienced cybersecurity teams, IT security organizational capabilities, and risk management help organizations enter new markets. With every expansion, there is a risk. Quality cybersecurity strategies reduce the risk of the new business venture by adopting already-proven protection and monitoring functions.Investment in Cybersecurity Technologies and Strategy
Organizations will gain business value through continuous improvement, monitoring, policy enforcement, and incident response. Developing and improving their cybersecurity maturity helps organizations adjust and change their proven processes and capabilities instead of reinventing the entire posture strategy to meet new business requirements. The corporate SecOps teams should include security controls and processes instead of being treated as a separate security function. Breaches have a direct impact on digital assets and the financial well-being of an organization. In a cybersecurity maturity model, SecOps should be the unified monitoring and response organization for all things security.Conclusion
As organizations digitally transform, cybersecurity is now a strategic business imperative that requires buy-in from the entire executive leadership to work together to mitigate risks. As a result, executives are looking to security leaders to determine the ideal cybersecurity investment and protection strategy. Cybersecurity costs are increasing for all businesses globally. Instead of relying on insurance to defer risk, they'll have to expand their IT security capabilities to manage and mitigate risk, and there will be financial consequences when these processes fail, and the organization is the victim of an attack. With regulatory momentum, government oversight of the digital economy will become more engaged; and we all know compliance does not equal better security. Hopefully, with CISO’s now integrated with corporate strategists’, broader risk and security awareness will provide less opportunity for cybercriminals. What this means to companies, however, is that risk management and cybersecurity will have to be better understood by the C-suite and a business-impacting priority for Boards of Directors. The board of director’s investment in cybersecurity is beginning to reflect not only the potential negative impact of an attack, but also the value of being able to continue to digitally transform the organization without increasing risk. Many board directors hire external auditing firms to evaluate the business, finances, and supply chains. Often, each independent audit will include results from a cybersecurity risk assessment within their respective reports, along with cybersecurity recommendations. These external firms will also perform a series of threat modeling engagements to test the cybersecurity risk management collaboration within the organization and how they handle cyber threats, incident response, and proof of effective system-wide monitoring. With the CISO in the boardroom, the management of business risk as well as the return on investment concerning technology and security investments will be more calculable, transparent and integrated into the overall business strategy.Organizations Struggle Implementing Compliance Requirements Including NIST & Zero Trust Mandates
Over the last year, we’ve seen a literally flood of government legislation and formal guidance concerning cybersecurity best practices. New mandates have been coming or to the cyber community fast
How to Implement an Effective Vulnerability Management Program
We’ve written considerably on Vulnerability Management, Vulnerability Assessments and Patching because they are so critical to preventing attacks. I’ve provided links to several of the most read blog posts we
The Fundamental Elements of Cyber Hygiene
Cyber Hygiene or IT hygiene involves best practices related to cybersecurity to protect your network and infrastructure from threats. It serves as the basic foundation for a proactive, systematic, and
Developing a Risk-Based Vulnerability Management Program A Real-Life Case Study
Custom Security Solutions Empower Organizations to Create Robust, Efficient Vulnerability Management Programs Vulnerability management exists for the purpose of identifying and remediating vulnerabilities in systems quickly before they are exploited. Vulnerabilities,
Taking a Risk-Based Approach to Patch Management
Designing and Implementing a Risk-Based Patch Management Program In this blog post, we wanted to take an additional step into explaining the benefits of quality vulnerability management, vulnerability assessments and patch
Security Leaders Grapple with Understanding Their Own Cybersecurity Risk – Part 2
Risk Management Comes Back into Focus – Part 2 In our last blog post, Security Leaders Grapple with Understanding Their Own Cybersecurity Risk – Part 1 we quoted a recent Forrester