Why MAZE Ransomware Attacks are So Devastating
Why MAZE Ransomware Attacks are So Devastating
MAZE ransomware is quickly becoming one of the most devastating strains of Windows ransomware that have infiltrated companies and organizations around the world and demanded that a Bitcoin or Cryptocurrency payment be made in exchange for the safe, private recovery of encrypted data.
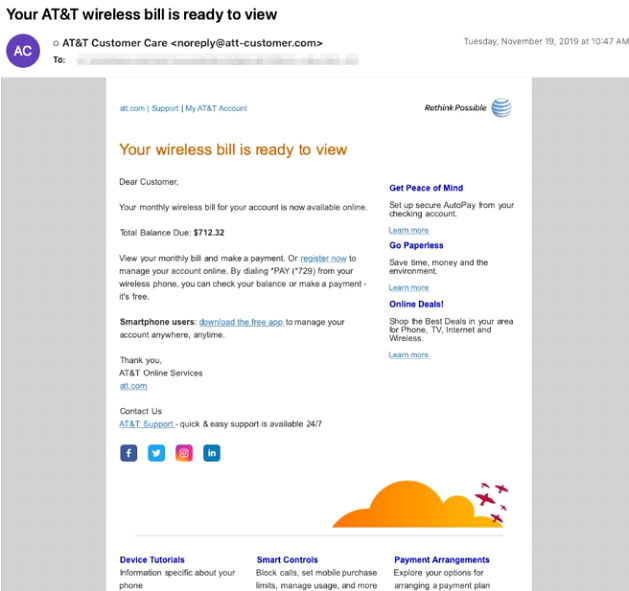
Cybercriminals have been actively deploying MAZE ransomware since at least last May. The ransomware was initially distributed via spam emails and exploit kits. These emails used tax, invoice, and package delivery themes with document attachments or inline links to documents that download and execute Maze ransomware. These emails were sent using a number of malicious domains created with the registrant address (gladkoff1991@yandex.ru). These emails used the subjects “Missed package delivery” and “Your AT&T wireless bill is ready to view” and were sent using a number of malicious domains with the registrant address abusereceive@hitler.rocks. MAZE operators are now shifting to deploying the malware post-compromise.
Why are MAZE Ransomware Attacks so Devastating?
A variety of criminal organizations are involved in MAZE ransomware operations. The criminals behind MAZE also maintain a public-facing website where they post data stolen from victims who refuse to pay an extortion fee. Mandiant identified multiple Russian-speaking actors who claimed to use MAZE ransomware and were seeking help to recruit new criminals to fill a variety of roles on their teams.
What makes MAZE such a significant threat to organizations is the fact that the attack both exposes sensitive data and disrupts enterprise networks. This is what makes MAZE more dangerous than most ransomware attacks; stealing the data it finds and exfiltrating it to servers controlled by malicious hackers who then threaten to release it if a ransom is not paid is another piece of leverage allowing criminals to collect bribe money more effectively.
MAZE Ransomware steals the data, encrypts it like other ransomware, however its operators also threaten to expose the data if the ransom is not paid, making the attacks a data breach as well.
Increasingly, other ransomware like REvil, better known as Sodinokibi, have been observed using similar tactics.
IT Services Organization Cognizant Becomes MAZE Attack Victim
In a series of data breach notifications, IT services giant Cognizant has stated that unencrypted data from several of its systems was most likely accessed and stolen during an April MAZE Ransomware attack. Cognizant is one of the largest IT managed services company in the world with close to 300,000 employees and over $15 billion in revenue. As a managed service provider or MSSP, Cognizant remotely manages the IT security functions of its many of its clients to monitor and manage logs, fix security-related vulnerabilities and install patches.
On April 17th, Cognizant began emailing their clients to warn them that they were under attack by the Maze Ransomware so that they could disconnect themselves from Cognizant and protect themselves from possibly being affected.
In two data breach notification letters filed with the Office of the Attorney General of California, Cognizant states that the Maze Ransomware operators were active on Cognizant’s network between April 9th and the 11th. During the time they had access, they “likely exfiltrated a limited amount of data from Cognizant’s systems.” In the Cognizant attack, before deploying ransomware and encrypting devices, the MAZE Ransomware operators first worked their way laterally through the network and to search for and steal sensitive, unencrypted files.
In addition, just last week, a U.S. nuclear missile contractor was hit by a MAZE ransomware attack that allowed hackers to access the organization’s sensitive information. Westech International is responsible for the maintenance of the U.S. arsenal of Minuteman III land-based intercontinental ballistic missiles (ICBM). The military contractor released a media statement saying a ransomware attack affected part of the company’s systems and encrypted some of the company’s files.
The criminal organization involved in the Westech ransomware attack is expected to attempt selling the data to a hostile nation to earn a higher payment. Court documents also reveal Russian intelligence agencies cooperate with hackers in obtaining highly classified information.
MAZE Operators Claim Over 100 Victims in 12 Months
Based on data gathered from incident reports, more than 100 alleged MAZE victims reported by various media outlets and on the MAZE website since November of last year. The victims are primarily based in North America, although in total they span nearly every geographical region and most industries including manufacturing, legal, financial services, construction, healthcare, technology, retail, and government. Their stolen files are then used as an extortion tactic by threatening to publicly release the data on the MAZE operator’s site if the victim does not pay the ransom.
As we suggested above, the reality is this is both a ransomware attack AND a data breach at the same time and is thus devastating for companies who become victims. The website operated by the criminals behind the MAZE attacks claims if the ransom is not paid, they will:
- Release public details of your security breach and inform the media
- Sell the stolen sensitive data on the black market
- Inform any stock exchanges on which your company is listed about the attack and the loss of sensitive information
- Use the stolen information to attack clients and partners as well as inform them that your company was hacked
What makes these ransomware attacks more destructive and disturbing than most is that the MAZE ransomware gang is not only capable of writing sophisticated malware that utilizes a variety of tools to search for passwords to move laterally, encrypt files, and avoid detection, they also found a very effective way of increasing the pressure on its corporate victims to pay the ransom.
According to the MAZE operator’s website they encrypt and exfiltrate “over 100Gb of data from a single client and sometimes up to 10Tb of commercial and private information. We are looking for NDA marked information and everything that can be used as a base for the lawsuit against our client.”
MAZE Operators Leverage a “Shaming” Website to Make “Clients” Pay
The MAZE operator’s website actually lists their “new clients” – the criminal’s term for recent corporate victims who have decided not to pay the ransom and who are likely trying to keep news of the attack out of the public eye.
The website includes details of when victims had their computer systems hit by the MAZE ransomware as well as links to downloads of stolen data and documents as proof of the breach. The site even has social media buttons so that visitors can share details of breaches with their network.
Conclusion
The MAZE criminals use a variety of different sophisticated tactics and techniques to infiltrate your network. This can include taking advantage of known vulnerabilities that have not been patched, remote desktop connections with weak passwords, and phishing attacks using malicious email attachments and/or links. In some cases, the attack may come from a friend, partner or customer of the business who has already fallen victim to the MAZE operators.
To protect yourself, you must backup your systems – it is the only fundamental way that you will have a chance at restoring your data. You should still be monitoring logs, running anti-virus solutions, firewalls, IDS/IPS and most importantly making sure your systems are protected with the latest patches to eliminate known vulnerabilities. Finally, unique passwords to protect sensitive data and accounts and multi-factor authentication are an essential layer of security.
In addition, organizations need to encrypt sensitive data or PII. Finally, as we have suggested a variety of times, phishing is the main attack vector used not only by MAZE, but also by most other types of attacks, you should still be educating and informing staff about risks and the methods used by cybercriminals to electronically infiltrate organizations.
To Learn More About How to Defend Against Ransomware Attacks or If You Have Been Attacked Please Call Us – as Always, We Are Happy to Help – 1 (888) 982-0678.
You Can Also Fill Out Our Contact Us Form Here to Talk with a Security Specialist – https://secureops.com/contact-us/







